Crypto exchanges have hot wallets and cold wallets. The wallets store user secret keys as well as the exchange’s secret keys. Most of the keys are stored offline in vaults (cold wallet). A portion of the keys are stored on servers connected to the internet (hot wallet) to facilitate transactions. These servers are susceptible to a data breach just like any other hacker attack.
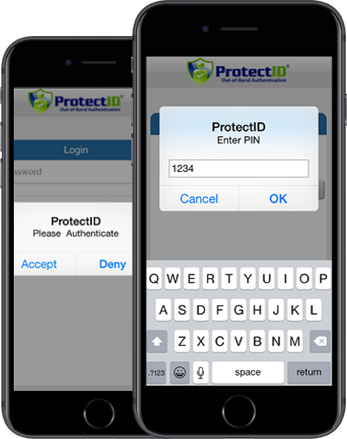
Exchange Defender comprises two products to protect the internal systems of the crypto exchange. These are – CryptoDefender™ (described earlier) and ProtectID®. ™protects the exchange’s computers and mobile devices from keylogging, screen capture and clickjack attacks. ProtectID® secures access to the internal systems via two factor out-of-band authentication. The ProtectID® system is shown below –
Authentication methods include:
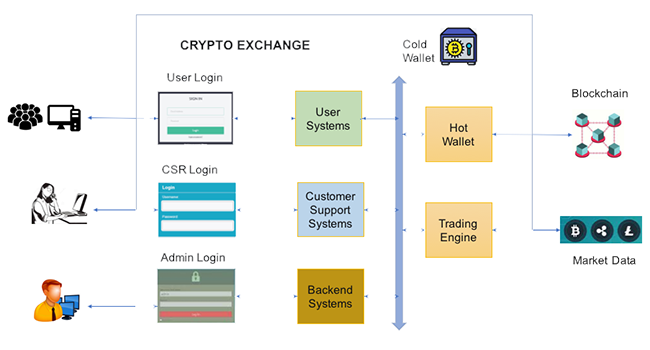
A typical crypto exchange architecture is shown below –
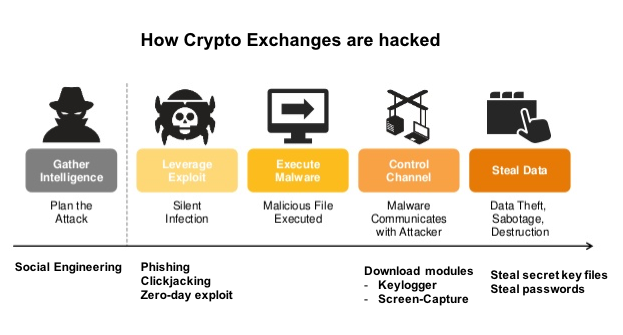
Case study - Crypto Exchange
Target - Financial
ExchangeDefender can secure the following vulnerability points –
| Vulnerability |
Endpoint Protection |
Login Authentication |
Transaction Authentication |
|---|---|---|---|
| User Login | X | X | - |
| CSR Login | X | X | - |
| Admin Login | X | X | - |
| Hot Wallet | - | - | X |
Interested in finding out more about BlockSafe Technologies? For media and investors contact us at:
(732) 661-9641
[email protected]
Securing the Blockchain Ecosystem:
Wallets, Exchanges, and Private Blockchains
